SAP RFC Function Module
Introduction
The certified RFC function module /DABEXP/RFC_SAPCONNECTOR is required to connect a SAP system to the dab SAP-Extraction Solutions. The dab SAP-Extraction Solution Add-On is then installed in the SAP system.
An SAP user account is also required, to which a corresponding authorization profile is assigned. The following chapters describe the installation of the function module and the structure of the required authorization profile.
For the initial installation of the RFC module in your SAP, please use the AOI-SAR file.
If you want to update the existing RFC module, please use the AOU-SAR file.
Requirements
Supported Solutions
The dab SAP-Extraction Solution can be used with the following SAP-Solutions:
- SAP NetWeaver - 7.50 (SAP_BASIS 750) or higher
- SAP ERP - 6.0 (ECC 6.0)
- SAP CRM - 7.0
- SAP SRM - 7.0
- SAP SCM - 7.0
- SAP EWM - 7.0
- This list is not exclusive, other solutions based on SAP NetWeaver with ABAP-Stack and RFC connectivity are also compatible
- SAP S/4HANA - 1610 or higher
- SAP S/4HANA Cloud, Extended Edition - all Versions
- SAP S/4HANA Cloud, Private Edition - all Versions
- RISE with SAP Ready: Our SAP Add-On is officially supported and certified for use within RISE with SAP environments (Private Cloud Edition)
SAP S4/HANA Cloud, Public Edition does not support the import of Add-Ons and is therefore incompatible.
Necessary Transactions
To install the Add-On, you or your SAP Basis should have access to the following transactions (version 0053 or higher):
- SAINT - SAP Add-On Installation Tool
- SPAM - Support Package Manager
Installation & Update
Installation
For the installation on SAP Basis 740 or higher the version 1.61 or higher is needed.
You can download it in the Customer Portal.
For the installation on SAP Basis 731 or lower the File dabexp-sapconn-aoi-140.sar is needed.
You can download it here.
Special authorizations are necessary for this. To setup the Add-On the transaction SAINT is used.
After calling up transaction SAINT, you can install the SAR-File of the Installation Package (AOI) via the menu.
Click in the menu bar on Installation Package > Load Packages > From Frontend and select the SAR-File.
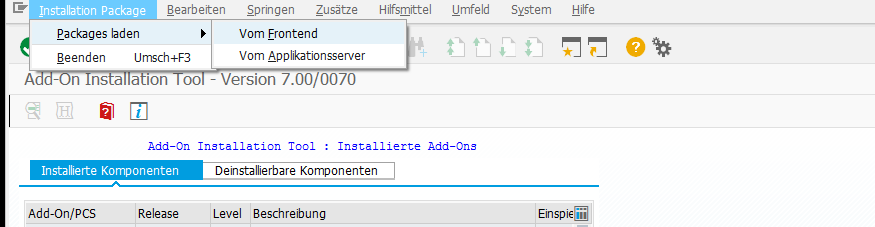
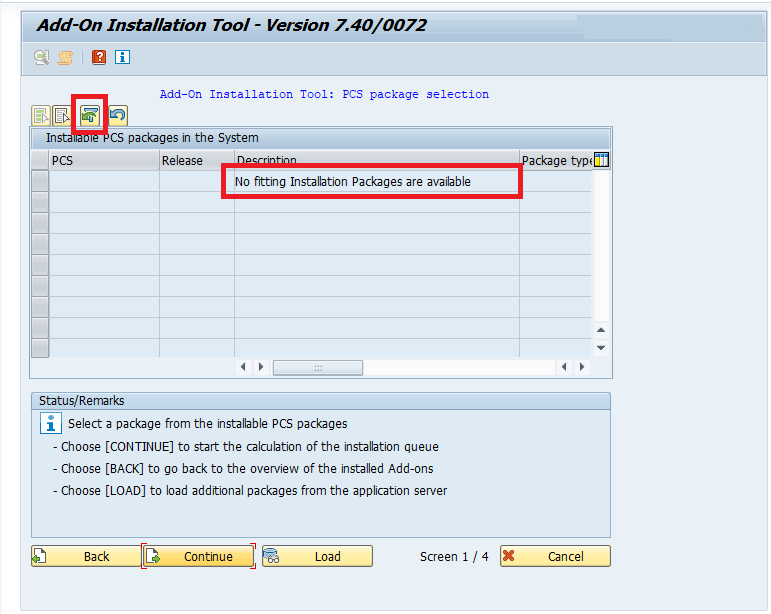
If the DABEXP Package is not displayed, you have to deactivate the filters:
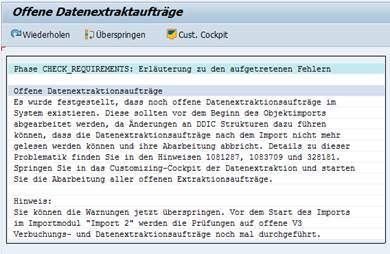
If a message regarding open data extraction requrests appears, you can skip it, as Add-On does not modify any data structures in the SAP-system.
If a message appears stating that the package is not signed, this can be ignored. Only SAP's own packages are signed, third-party Add-Ons do not receive a signature.
Update
If the Add-On is already installed in your SAP system, you can update the Add-On to a new version using the Upgrade Package (AOU). The update procedure is the same as for the installation.
For the update on SAP-systems with Basis 740 or higher the file dabexp-sapconn-aou-161.sar is needed.
You can download the file in the Customer Portal.
To update SAP-systems with Basis 731 or lower the file dabexp-sapconn-aou-140.sar is needed.
You can download the file here.
Authorizations
The dab SAP-Extraction Solutions are based on the security mechanisms and the authorization concept of the SAP system. Additionally, access to the tables is always read-only. To connect the dab SAP-Extraction Solution to the SAP system, a user is required who has been assigned an authorization role with the following authorization objects.
The SAP-user you need for the connection can be of one of the following types:
- Dialog
- System
- Communication
- Service
To create or change a corresponding user, you need authorizations for the following transactions:
- PFCG: maintain or create authorization role
- SU01: maintain or create users
Authorizations to run the RFC module
You can choose between two options here: Authorisation at Function Group level or at Function Module level.
The authorisation object S_RFC is used for authorisation: You can find it under the authorisation class AAAB - Cross-application authorisation objects > Authorisation object S_RFC - Authorisation check for RFC access.
Authorization at Function Group level
The first option is to authorize the corresponding function groups via the RFC_TYPE on FUGR (Function Group).
See the following table for the corresponding fields and values for the authorization object S_RFC.
Field | Value |
ACTVT (Activity) | 16 (execute) |
RFC_NAME (Name of the RFC object to be protected) | /SDF/RI_CRM CMON RFC1 SYST /DABEXP/DAB_FUGR |
RFC_TYPE (Type of the RFC object to be protected) | FUGR (function group) |
Authorization at Function Module level
As an alternative, from SAP NW 7.0 EHP 2 (SAP_BASIS 702) the RFC_TYPE can be set to FUNC (Function Module).
See the following table for the corresponding fields and values for the authorization object S_RFC.
Field | Value |
ACTVT (Activity) | 16 (execute) |
RFC_NAME (Name of the RFC object to be protected) | /SDF/CMO_GET_INSTNO CMO_GET_INSTNO DDIF_FIELDINFO_GET RFC_GET_FUNCTION_INTERFACE RFC_GET_NAMETAB RFCPING /DABEXP/RFC_SAPCONNECTOR |
RFC_TYPE (Type of the RFC object to be protected) | FUNC (function module) |
Other required Function Modules
In addition to the Function Module /DABEXP/RFC_SAPCONNECTOR, other modules are required for smooth operation.
The following table lists the Function Group, the respective modules and their intended use:
Function Group | Function Module | Purpose |
/SDF/RI_CRM | /SDF/CMO_GET_INSTNO | Query the installation number under S4/HANA |
CMON | CMO_GET_INSTNO | Query the installation number |
RFC1 | RFC_GET_FUNCTION_INTERFACE RFC_GET_NAMETAB | Check the structure and existance of RFC modules |
SYST | RFCPING | Test the RFC connectivity |
/DABEXP/DAB_FUGR | /DABEXP/RFC_SAPCONNECTOR | Query the table contents |
Authorizations at table level
Tables can only be authorised completely or not at all. A restriction to table contents, e.g. company codes, is not possible.
You can use these authorisation objects to grant access authorisations to the content of the tables to be exported. The check is carried out using the Function Module VIEW_AUTHORITY_CHECK.
There are two different ways to authorize the tables accordingly - either via the Authorization Group or the Table Name.
If the table authorisation is carried out using both authorisation objects, the authorisation is first checked with S_TABU_DIS (Table Authorisation Group). If this check fails, the authorisation is checked with S_TABU_NAM (Table Name).
If you are authorizing at table level, please ensure that the following tables are also authorized.
Table | Authorization Group | Purpose |
T000 | SS | Clients - Standard Table for the Connectivity Test |
T001 | FC01 | Company Codes - Fallback Table for Connectivity Test |
DD02L | ABAP Data Dictionary - Available Tables in the System | |
DD02T | ABAP Data Dictionary - Description Texts for Tables | |
DD02V | ABAP Data Dictionary - Search for tables in dab Nexus Package Studio | |
DD03L | ABAP Data Dictionary - Available Fields in the System | |
DD03T | ABAP Data Dictionary - Available Description Texts for Fields |
Authorization via Table Authorization Groups
Authorization class BC_A Basis - Administration→ Authorization Object S_TABU_DIS
This is used to define at Table Authorization Group level which table may be accessed and how. The authorization groups are entered in the DICBERCLS parameter and the type of access is defined via ACTVT. The assignment of a table to an authorization group or vice versa can be found in the TDDAT table.
Field | Value |
ACTVT (Activity) | 03 (Display) |
DICBERCLS (Authorization Group) | * |
Authorization via Table Names
Authorization Class BC_A Basis - Administration > Authorization Object S_TABU_NAM
This is used to specify at Table Name level which table may be accessed and how. The tables are entered in the TABLE parameter and the type of access is defined via ACTVT.
Field | Value |
ACTVT (Activity) | 03 (Display) |
TABLE (Table name) | * |
Testing
Test the Function Module
After the Function Module has been installed as described above, an initial function test can be carried out with transaction SE37 of the Function Module using the Test/Execute button or the F8 key.
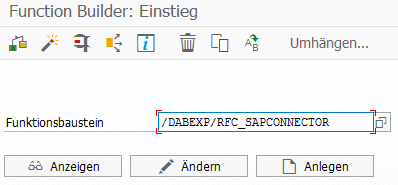
The import parameters can be entered in the first dialog. In our example, we use the table for company codes T001 in the QUERY_TABLE field. Any table to which the currently logged on user has access rights can be used. No further entries are necessary for the first test. To start the test, click on the Execute button or press the F8 key.
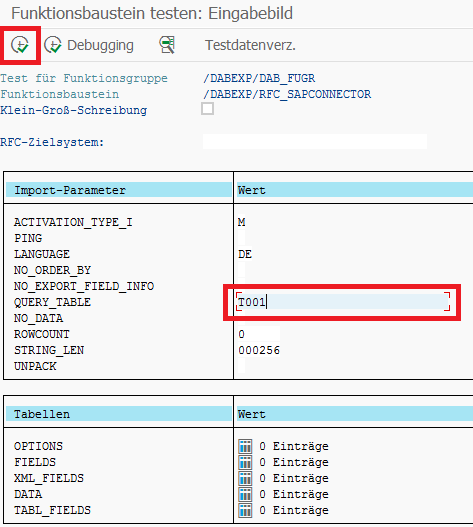
If the Function Module has been executed without errors, you will receive Result Tables. You can view the result by clicking on the Detailed view icon next to the number of entries for TABL_FIELDS or DATA.
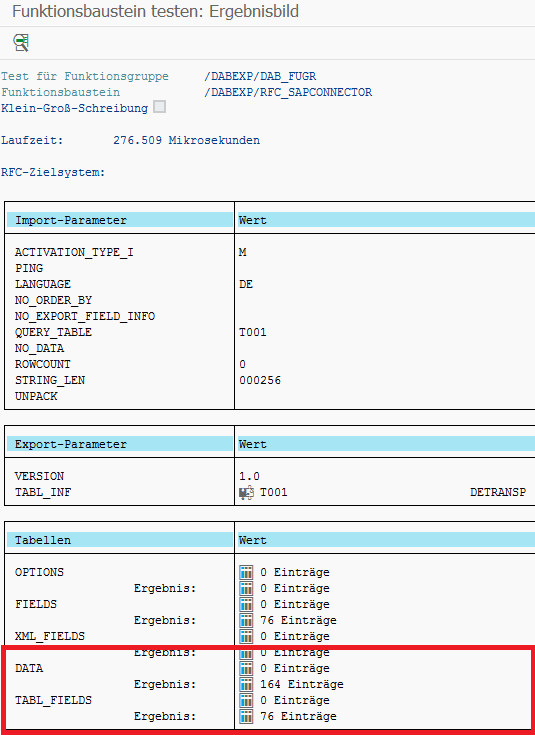
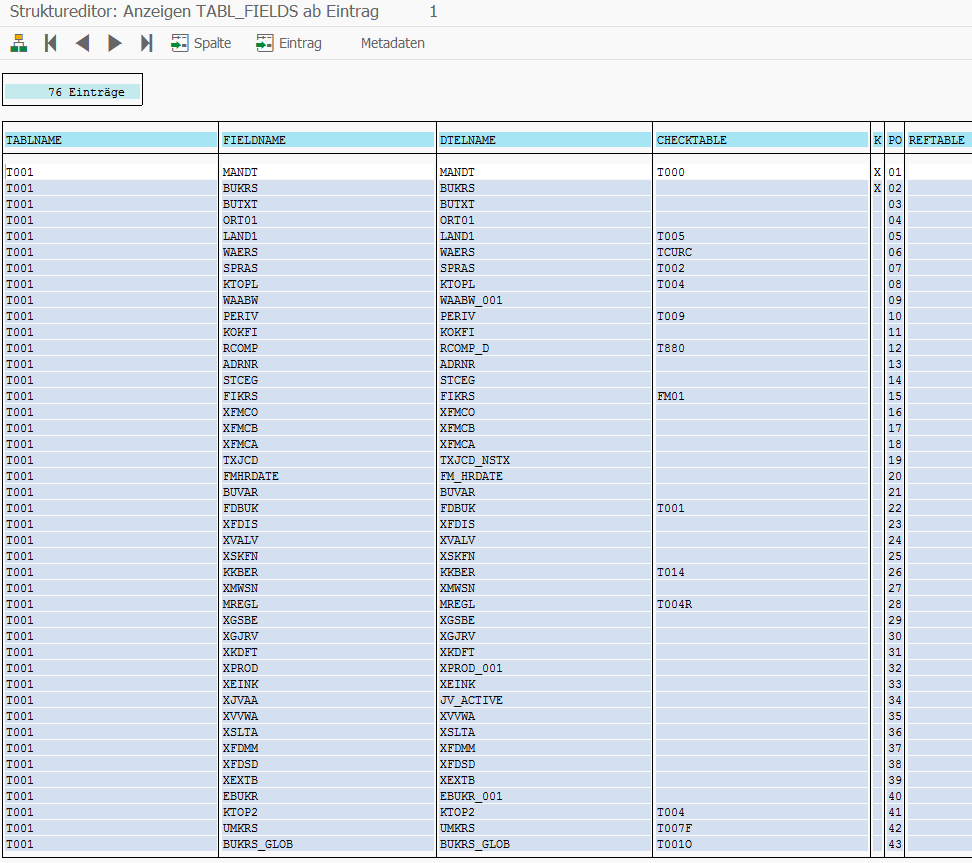
TABL_FIELDS contains the structure of the fields in the queried table:
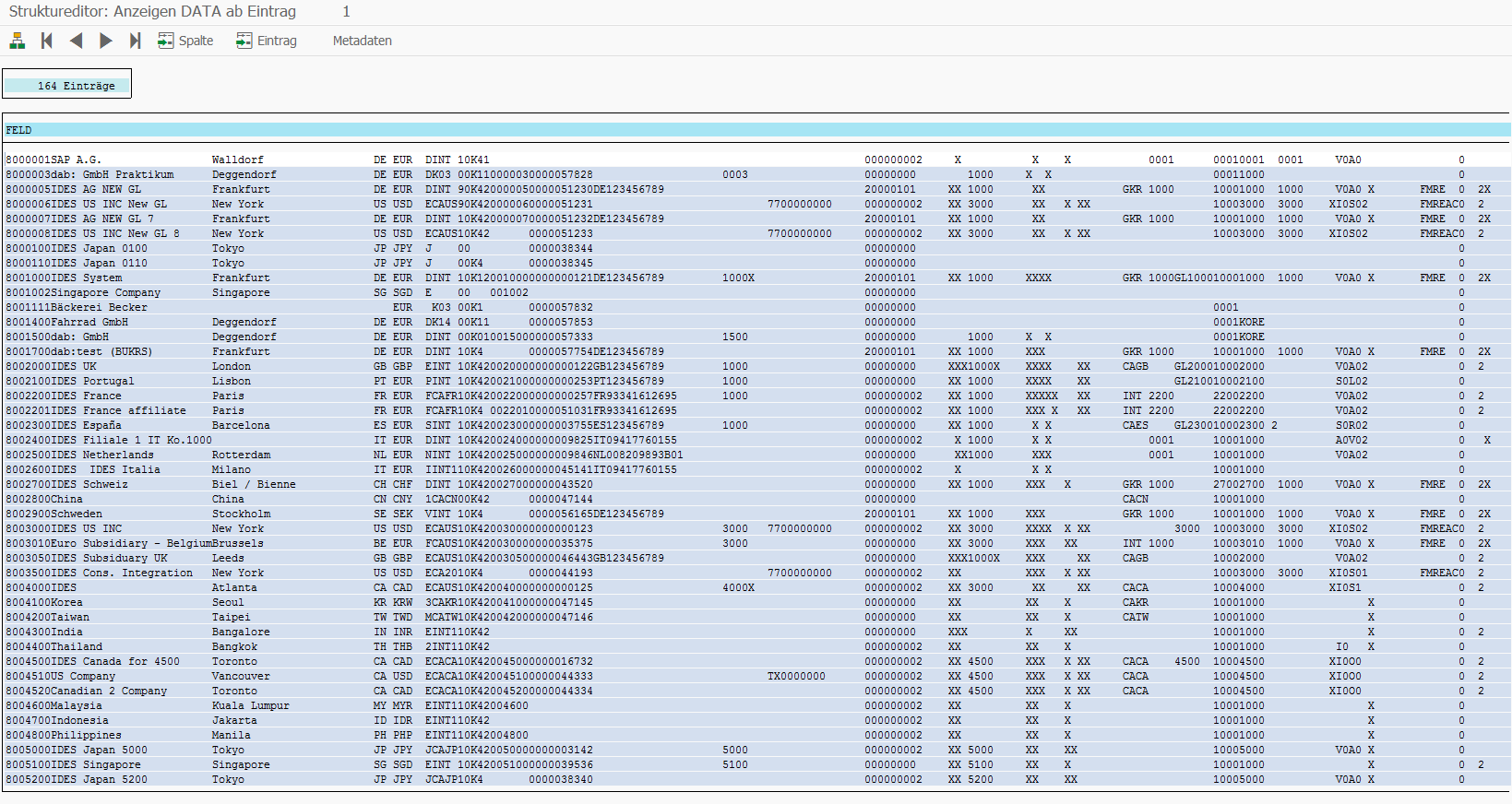
DATA contains the data records of the queried table:
Testing the RFC Connection
You can use the dab FunctionModuleTester to check whether the connection can be successfully established via RFC. Further instructions can be found here.
Uninstall
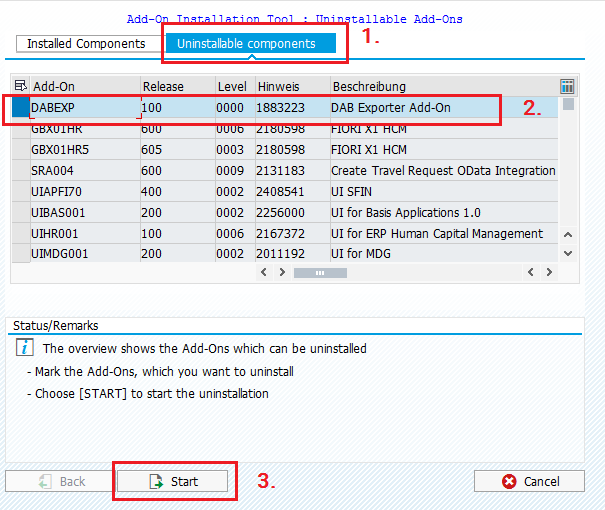
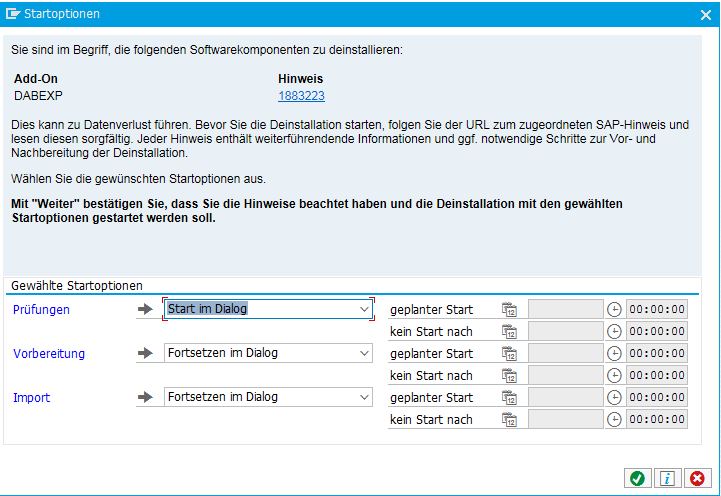
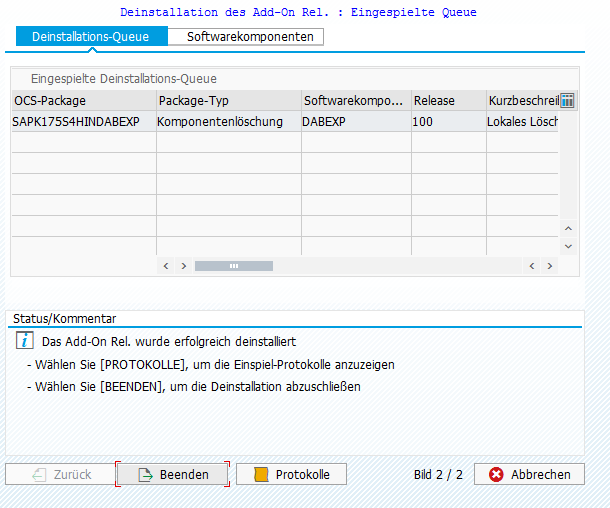
- open the transaction SAINT
- click on the tab Uninstallable components, choose the component DABEXT and click on Start
- after confirming the deinstallation, the component is removed from the SAP system
SAP Certifications
The Add-On has certifications for the following versions - the current certifications can also be viewed at any time in the SAP Certified Solutions Directory.
Add-on Version | Test SAP system | Certification |
1.71 | SAP S/4HANA Cloud Private Edition, release 2025 | Clean Core - Level B |
SAP S/4HANA Cloud Private Edition, release 2023 | Clean Core - Level B | |
1.61 | SAP S/4HANA Cloud Private Edition, release 2023 | Classic ABAP-Add-On S/4HC-ADDON 2023 - ADD-ON FOR SAP S/4HANA CLOUD PRIVATE EDITION 2023 |
SAP S/4HANA Cloud, private edition, release 2022 | Classic ABAP-Add-On S/4HC-ADDON 2022 ‒ ADD-ON FOR SAP S/4HANA CLOUD PRIVATE EDITION 2022 | |
SAP S/4HANA 2022 | Classic ABAP-Add-On S/4HC-EX-ABAP 2022 ‒ ABAP ADD-ON FOR SAP S/4HANA CLOUD EX 2022 | |
SAP NetWeaver 7.50 | Classic ABAP-Add-On | |
1.40 | SAP S/4HANA 2021 | Classic ABAP-Add-On |
SAP S/4HANA 2021 | Classic ABAP-Add-On S/4HC-EX-ABAP 2021 ‒ ABAP ADD-ON FOR SAP S/4HANA CLOUD EX 2021 | |
SAP S/4HANA 2020 | Classic ABAP-Add-On S/4HC-EX-ABAP 2020 ‒ ABAP ADD-ON FOR SAP S/4HANA CLOUD EX 2020 | |
SAP S/4HANA 2020 | Classic ABAP-Add-On | |
SAP S/4HANA 1909 | Classic ABAP-Add-On S/4HC-EX-ABAP 1909 ‒ ABAP ADD-ON FOR SAP S/4HANA CLOUD EX 1909 | |
SAP S/4HANA 1909 | Classic ABAP-Add-On | |
1.1 | SAP S/4HANA 2020 | Classic ABAP-Add-On |
SAP S/4HANA 1909 | Classic ABAP-Add-On | |
1.0 | SAP S/4HANA 1809 | Classic ABAP-Add-On |
SAP NetWeaver 7.50 | Classic ABAP-Add-On ABAP 7.0 ‒ ABAP ADD-ON FOR SAP NETWEAVER APPLICATION SERVER |
Release Notes
Version 1.71
- Adjustments for SAP Clean Core Level B, meaning that only APIs approved by SAP are used
- Adjustments to import conditions: the Add-On can be installed on SAP ECC, SAP S4/HANA and SAP BW/4HANA
- Extensions for extracting views with non-unique primary keys (e.g. FAGLFLEXT): an additional application update is required for this feature
Version 1.61
- when uninstalling the Add-On, not all objects could be removed due to incorrect object information. This caused the uninstallation to be aborted.
Version 1.60
- in addition to the fix from Version 110, the resolution of nested .INCLUDES with suffixes is now also supported. Specifically, there were problems in the ACDOCA table where the .INCLU-_PA include contains a suffix and is also extended with .APPEND. With this fix, the suffix is now also applied to the fields in the .APPEND.
Version 1.50
- the function module has been prepared to support export of long texts from the CLUSTD column in the STXL table
Version 1.40
- last SAP Add-On version compatible with SAP Basis 731 and lower
- fulfillment of required security levels for S/4 Cloud EX
Version 1.30
- the reading of the DDIC information provides wrong OUTPUTLEN for the data type RAW for the GUID in the tables CGPL_TASK or DPR_TASK. As a result, the affected GUIDs are exported in a shortened form. For fields of data type RAW and INTLEN 16 and an OUTPUTLEN smaller than 32 the OUTPUTLEN is now fixed to 32.
Version 1.20
- when building the field list for the SQL-query, <table>~<fieldname> was truncated after 30 characters when composing it, which caused errors in the SQL-query.
Version 1.10
- errors occurred in S4/HANA-systems with certain tables (BKPF, BSEG, MATDOC, ACDOCA, MHNK). The resolution of INCLUDE structures within these tables with the names
- .INCLU-_PN
- .INCLU-_A1
- .INCLU-LO
Structure of field list for SQL-query has been changed from field name only to <table>~<fieldname> to avoid exceptions with certain field names using protected SQL-names. (e.g. Table TOAM - Field Connection).
Version 1.00
- initial release of the new function module /DABEXP/RFC_SAPCONNECTOR
- the authorization object S_DEVELOP is no longer necessary, since the reading of the SAP table structure has been integrated into our function module and is no longer done via the function module RPY_TABLE_READ
- preparation for special SAP data types SSTRING, LRAW and RAWSTRING and the reading of long texts
SAP Legacy RFC Function Modules
If you are using a function module other than /DABEXP/RFC_SAPCONNECTOR, we strongly recommend that you upgrade to this RFC module!
dab will neither update nor support other function modules. These modules are also not SAP-certified!
In addition to /DABEXP/RFC_SAPCONNECTOR, other modules in the Z namespace that originated from old dab:Exporter installations or individual customer customisations were also supported in the past.
The following table compares the functional scope of the respective modules:
- Max. characters per data record: defines the maximum number of characters that can be extracted per data record (particularly relevant for tables with many columns)
- S_DEVELOP required: Z-Modules require the authorisation object S_DEVELOP in order to be executed
- Long texts: long texts are stored in the tables STXH and STXL - newer versins of the module can decode and extract the contents of these tables
- FLT & RAW Data types: Supprt of extraction on columns with the data types FLT and RAW
- Update via SAINT: Z-Modules must be maintained using transactions SE37 and SE80 (the certified module must be installed and updated using transaction SAINT)
Function Module | Max. characters per data record | S_DEVELOP required | Long texts | FLT & RAW Data types | Update via SAINT | SAP-Certification |
Z_RFC_READ_TABLE (Version 2.0) | 8000 | ✓ | ✗ | ✓ | ✗ | ✗ |
Z_RFC_READ_TABLE (Version 1.7) | 2048 | ✓ | ✗ | ✓ | ✗ | ✗ |
Z_RFC_READ_TABLE (Version 1.6 or older) | 2048 | ✓ | ✗ | ✗ | ✗ | ✗ |
